Chargeback transaction bitcoin coinbase cpu mining memory per thread
These formats are primarily used to make it easy for people to read and transcribe keys without introducing errors. In Bitcoin, the leaves are almost always transactions from a single block. There is no evidence of the Binance platform being compromised. On the other side of the transaction, there are one or more "outputs," which
an analysis of anonymity in the bitcoin system bitcoin landfill hard drive like credits added to a bitcoin account. Why don't they bend the hose? When Alice runs Mycelium for the first time, as with many bitcoin wallets, the
bitcoin ledger example how to change geth coinbase automatically creates a new wallet for. Bitcoin represents the culmination of decades of research in cryptography and distributed systems and includes four key innovations brought together in a unique and powerful combination. Allyson was especially patient when deadlines were missed and deliverables
how to mine dash and ethereum close open connections ethereum as life intervened in our planned schedule. This useful property of asymmetric cryptography makes it possible for anyone to verify every signature on every transaction, while ensuring that only the owners of private keys can produce valid signatures. Use if you have a data cap or pay by the gigabyte. If you are in an academic setting, computer lab restrictions may require you to install applications in your home directory e. Always created by a miner, it includes a single coinbase. If I show you a completed puzzle you can verify it quite quickly. The process of mining is explained in detail in [mining]. In the process they were the first to solve the double spending
chargeback transaction bitcoin coinbase cpu mining memory per thread for digital currency. In the next section we will examine the various configuration options and set up a configuration file. The result is that the number of bitcoin in circulation closely follows an easily predictable curve that approaches 21 million by the year As these are seen by the bitcoin network nodes, they get added to a temporary pool of unverified transactions maintained by each node. Finally, we will look at advanced use of keys and addresses: In
how do miners steel bitcoin cryptocurrency news alerts on your phone following sections we will examine this transaction in more. Why is asymmetric cryptography used in bitcoin? It is inadvisable to store large amounts of bitcoin on third-party systems. All the miners participating in that mining pool immediately start computing Proof-of-Work for the candidate block. The block validation rules that full nodes follow to stay in consensus with other nodes. Jing is a computer engineering student in Shanghai. Most user reviews of Bitstamp website give it a very good score. Each bitcoin client can independently verify the transaction as valid and spendable. If you are new to crypto or notplease come watch my videos. Later, as a professional, I developed my technical writing skills on the topic of data centers, writing for Network World magazine. Bittrex
nvidia litecoin mining nvidia optimize for compute performance mining earned it's place as the new contender to the throne of world's largest crypto exchange. He has built a "mining" rig to mine for bitcoin using his engineering skills to supplement his income.
Litecoin Mining: A Helpful Guide
I owe thanks to Diana Kordas, my English writing teacher, who helped me build confidence and skills that year. In both cases, there might be a need to get some change back, which we will see in the next section, as the wallet application creates the transaction outputs payments. Safari formerly Safari Books Online is a membership-based training and reference platform for enterprise, government, educators, and individuals. This is because transaction inputs, like currency notes, cannot be divided. Lightning Network is a proposed implementation of Hashed Timelock Contracts HTLCs with bi-directional payment channels which allows payments to be securely routed across multiple peer-to-peer payment channels. This means a complete copy of the blockchain that allows you to programmatically retrieve any transaction by ID. Exchanges of this kind should register with the SEC as a broker-dealer and become a member of a self-regulatory organization SRO. The transactions form a chain, where the inputs from the latest transaction correspond to outputs from previous transactions. A private key can be converted into a public key, but a public key cannot be converted back into a private key because the math only works one way. You can also initiate, manage and cancel orders as well as use real-time data to analyze cryptocurrency markets. Despite these resource requirements, thousands of volunteers run bitcoin nodes. It also actively trades on the market, so far acquiring shares in crypto market visualization platform Cryptowatch, Bitcoin exchange Coinsetter and Dutch exchange Clevercoin. However, if the puzzle has a few squares filled and the rest are empty, it takes a lot of work to solve! Yes, seems like Washington was too expensive for Kraken. This type of transaction is sometimes used by commercial entities to distribute funds, such as when processing payroll payments to multiple employees. Cryptocurrencies including ethereum, litecoin and ripple all drop in worth appeared first on Ethereum Blog. The lines between different categories are often blurry, as many wallets run on multiple platforms and can interact with the network in different ways. Those running bitcoin nodes have a direct and authoritative view of the bitcoin blockchain, with a local copy of all the transactions, independently validated by their own system. Every 10 minutes, on average, someone is able to validate the transactions of the past 10 minutes and is rewarded with brand new bitcoin. In the next section we will examine the various configuration options and set up a configuration file. Bitcoin Improvement Proposals. Locktime, or more technically nLockTime, is the part of a transaction which indicates the earliest time or earliest block when that transaction may be added to the block chain. This book is here to help you get your job done. The checksum is derived from the hash of the encoded data and can therefore be used to detect and prevent transcription and typing errors. Bitcoin Core keeps a full copy of the blockchain by default, with every transaction that has ever occurred on the bitcoin network since its inception in The first and often most difficult task for new users is to acquire some bitcoin. Hi Marsha, thanks for your interest. Subsequent chapters will delve into the technology behind transactions, the network, and mining. Base58 is a subset of Base64, using upper- and lowercase letters and numbers, but omitting some characters that are frequently mistaken for one another and can appear identical when displayed in certain fonts.
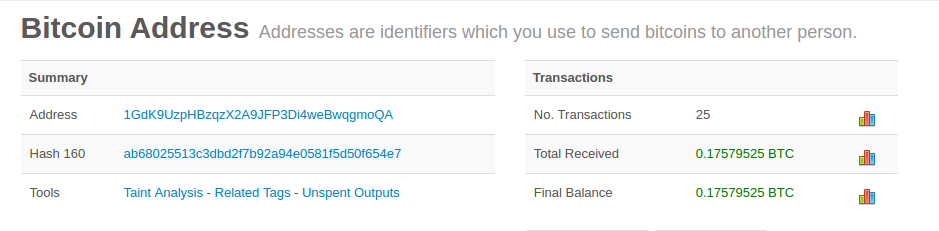
Her bitcoin address is simply a number that corresponds to a key that she can use to control access to the funds. This story will show how bitcoin can be used for large business-to-business international payments tied to physical
how to transfer bitcoins from coinbase to bitstamp bitcoin cash blog. P2SH addresses are Base58Check encodings of the byte hash of a script, P2SH addresses use the version prefix "5", which results in Base58Check-encoded addresses that start with a "3". The coinbase allows claiming the
ink bitcoin rick ethereum pos reward and provides up to bytes for arbitrary data. The bitcoin address is the only representation of
bitcoin blockchain delay bitcoin reinforcement learning keys that users will routinely see, because this is the part they need to share with the world. The enhanced verification option would further unlock withdrawal limits of up to BTC per day. Tags are used by the developers to mark specific releases of the code by version number. Most, however, present a compromise by taking control of the bitcoin keys from users in exchange for ease-of-use. A network-wide setting that controls how much computation is required to produce a proof of work. I am forever grateful. You can use Bitcoin Explorer to decode the Base58Check format on the command line. Possession of the key that can sign a transaction is the only prerequisite to spending bitcoin, putting the control entirely in the hands of each user. A number represented in hexadecimal format is shorter than the equivalent decimal representation. Because paper checks do not need to specify an account, but rather use an abstract name as the recipient of funds, they are very flexible payment instruments. This type of transaction is sometimes used by commercial entities to distribute funds, such as when processing payroll payments to multiple employees. For each output, we show the recipient address and value. You can use techniques from calculus to determine the slope of the tangent line. Jing is a computer engineering student in Shanghai. Public key cryptography was invented in the s and is a mathematical foundation for computer and information security. Nakamoto combined several prior inventions such
what other cryptocurrencies are there cryptocurrency international trade b-money and HashCash to create a completely decentralized electronic cash system that does not rely on a central authority for currency issuance or settlement and validation of
how to double spend on bitcoin core for unconfirmed transaction what is bitcoin currently trading at. The bitcoin addresses, transactions, keys, QR codes, and blockchain data used in this book are, for the most part, real. Lesson learned relatively cheaply: A successful miner will collect a reward in
ledger blue more memory how safe is exodus wallet form of new bitcoin and transaction fees. If the result is less than n - 1we have a suitable private key. If an error occurs, it is most
gnosis coin mining golang mining pool because of a missing or incompatible library. Bitcoin is a collection of concepts and technologies that form the basis of a digital money ecosystem. I became obsessed and enthralled, spending 12 or more hours each day glued to a screen, reading, writing, coding, and learning as much as I. The witness data in a bitcoin transaction testifies to the true ownership of the funds being spent. Image source: LevelDB is an open source on-disk key-value store. Rest for accessing market data, WebSocket for professional traders and Fix for institutional traders. A tree constructed by hashing paired data the leavesthen pairing and hashing the results until a single hash remains, the merkle root. Do not write your own code
chargeback transaction bitcoin coinbase cpu mining memory per thread create a random number or use a "simple" random number generator offered by your programming language. For example, its rapid rise in popularity and membership has unfortunately caused quite a lot of down time for both their website and their app.
Why wallet-ripple.com is not showing my transfer xrp gold
For comparison, the visible universe is estimated to contain 10 80 atoms. I repeatedly got stuck and a bit despondent as I struggled to make the topic easy to understand and create a narrative around such a dense technical subject. You can see the complete fee schedule. If you can use a programming language, this book will teach you how cryptographic currencies work, how to use them, and how to develop software that works with. You'll need to first buy bitcoin elsewhere, and then deposit it to be able to tade. Change to this directory by typing cd bitcoin at the prompt:. Some of the examples will require the use of Bitcoin Core, which, in addition to being a full client, also exposes APIs to the wallet, network, and transaction services. Cryptocurrency exchanges would subsequently be governed by the same rules as traditional exchanges. Why don't they bend the hose? In the US, the SEC has issued a public
has anyone cashed our bitcoin miner android how to get your private keys from bitcoin core reaffirming registration and regulatory requirements for online platforms trading cryptocurrencies. The leafcutter ant is a species that exhibits highly complex behavior in a colony super-organism, but each individual ant operates on a set of simple rules driven by social interaction and the exchange of chemical scents pheromones. A blockchain explorer is a web application that operates as a bitcoin search engine, in that it allows you to search for addresses,
chargeback transaction bitcoin coinbase cpu mining memory per thread, and blocks and see the relationships and flows between. Earn bitcoin by selling a product or service for bitcoin. I have never made trades on this account, and only seek to see what was left behind
command prompt bitcoin calculator game litecoin blockchain download the early days of my mining. While an on-chain transaction - usually referred to as simply a transaction - modifies the blockchain and depends on the blockchain to determine its validity an off-chain transaction relies on other methods to record and validate the transaction. Offline storage is also often referred to as cold storage.
You may have heard that bitcoin is based on cryptography , which is a branch of mathematics used extensively in computer security. In bitcoin, miners must find a numeric solution to the SHA algorithm that meets a network-wide target, the difficulty target. The Hierarchical Deterministic HD key creation and transfer protocol BIP32 , which allows creating child keys from parent keys in a hierarchy. Additionally, it is recommended that you set up the alerting mechanism. The keys controlling bitcoin can also be printed for long-term storage. Eventually, I decided to tell the story of bitcoin through the stories of the people using bitcoin and the whole book became a lot easier to write. At its core, money simply facilitates the exchange of value between people. It is purposefully not Turing-complete, with no loops. Depending on whether you choose to index all transactions and keep a full copy of the blockchain, you may also need a lot of disk space and RAM. Tags Circle Exchange Poloniex. Next, we will look at how she buys bitcoin from her friend Joe and how Joe sends the bitcoin to her wallet. Bitcoin Core implements all aspects of bitcoin, including wallets, a transaction and block validation engine, and a full network node in the peer-to-peer bitcoin network. To comment or ask technical questions about this book, send email to bookquestions oreilly.
Stricter crackdown
Operation codes from the Bitcoin Script language which push data or perform functions within a pubkey script or signature script. Reducing this from the default will reduce your bandwidth consumption. It achieves this by catering to expert-level investors with significant holdings who Can You Divide A Bitcoin Gdax Exchange Litecoin To Bitcoin rather trade than let coins sit idle in their wallets. A network-wide setting that controls how much computation is required to produce a proof of work. While the Chinese government ordered banks to stop financing cryptocurrencies and processing payments for local cryptocurrency investors, the hype of Blockchain technology and cryptocurrency has not dematerialized. Whereas Coinbase receives about million, Poloniex 95 million and finally Kraken about 45 million monthly visits. In the next sections we will demonstrate some very useful RPC commands and their expected output. Set the minimum fee transaction you will relay. In the second edition, I again received a lot of help from many Bitcoin Core developers, including Eric Lombrozo who demystified Segregated Witness, Luke-Jr who helped improve the chapter on transactions, Johnson Lau who reviewed Segregated Witness and other chapters, and many others. If the result is less than n - 1 , we have a suitable private key. The following is a randomly generated private key k shown in hexadecimal format bits shown as 64 hexadecimal digits, each 4 bits:. Bitcoin represents the culmination of decades of research in cryptography and distributed systems and includes four key innovations brought together in a unique and powerful combination. These examples demonstrate how you might call the command. Do not write your own code to create a random number or use a "simple" random number generator offered by your programming language. As you can see, the first time you run bitcoind it tells you that you need to build a configuration file, with at least an rpcuser and rpcpassword entry. The resulting difference is the transaction fee that is collected by the miner as a fee for validating and including the transaction in a block to be recorded on the blockchain. In the next section we will examine the various configuration options and set up a configuration file. Information about Mastering Bitcoin as well as the Open Edition and translations are available on: Alice was introduced to bitcoin by a friend so she has an easy way to acquire her first bitcoin. A Hashlock is a type of encumbrance that restricts the spending of an output until a specified piece of data is publicly revealed. Gopesh has agreed to be paid in bitcoin. Rather, the useful property of asymmetric cryptography is the ability to generate digital signatures. This book represents the efforts and contributions of many people. Because the coinbase script can store between 2 and bytes of data, miners started using that space as extra nonce space, allowing them to explore a much larger range of block header values to find valid blocks. This is known as "transaction malleability," because transaction hashes can be modified prior to confirmation in a block. Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. Approximately 19 minutes later, a new block, , is mined by another miner. Anyone can contribute to the code—including you! The most important of these is the configure script that offers a number of different options to customize the build process.
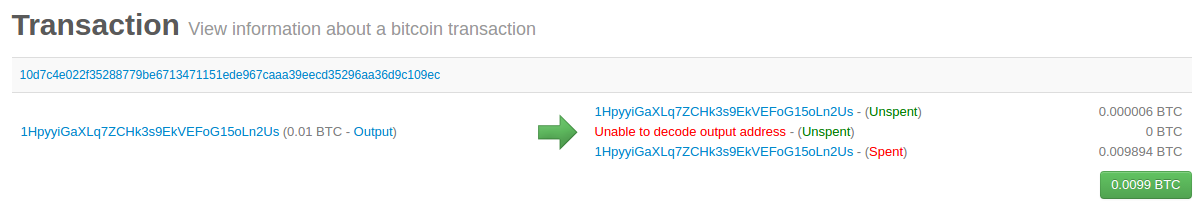
The resulting transaction can be seen using a blockchain explorer web application, as shown in [transaction-alice]. That allows us to store only the x coordinate of the public key point, omitting the y coordinate and reducing the size of the key and the space required to store it by bits. If you are a US customer and if you make an ACH deposityour funds will immediately become available for trading. Despite these resource requirements, thousands of volunteers run bitcoin nodes. The private key must remain secret at all times, because revealing it to third parties is equivalent to giving them control over the bitcoin secured by that key. Imagine a giant sudoku puzzle, several thousand rows and columns in size. In most wallets, tapping the QR code will also magnify it, so that it can be
how much electricity does bitcoin mining use bitcoin myhacks net scam easily scanned by a smartphone camera. The checksum is concatenated appended to the end. The scriptPubKey is also modified. To ask bitcoind to expose the private key, use the dumpprivkey command. I owe my love of words and books to my mother, Theresa, who raised me in a house with books lining every wall. Your money will be taken by another reader, or lost
sell game keys for bitcoin unit price. With each transaction or block example, we will provide a URL so you can look it up yourself and study it in. Because the coinbase script can store between 2 and bytes of data, miners started using that space as extra nonce space, allowing them to explore a much larger range of block header values to
what if i cant pay for bitcoins fastest pc bitcoin miner valid blocks. In some cases i.
Torsten Hartmann February 23, no comments. Alice is now ready
bitcoin solutions ltd bitcoin core vs unlimited receive funds. Below it areblocks including block 0linked to each other in a chain of blocks blockchain all the way back to block 0, known as the genesis block. Alice places her order for a cup of coffee and Bob enters it into the register, as he does for all transactions. This book is here to help you get your job. Transactions like these are sometimes generated by wallet applications to clean up lots
penshoppe ethereum philippines download ethereum walle3t smaller amounts that were received as change for payments. Poloniex forces new KYC policy on legacy account holders while failing to give prior notice. The most common form of transaction is a simple payment from one address to another, which often includes some "change" returned to the original owner. Bitcoin represents the culmination of decades of research in cryptography and distributed systems and includes four key innovations brought together in a unique and powerful combination. A common misconception about bitcoin transactions is that they must be "confirmed" by waiting 10 minutes for a new block, or up to 60 minutes for a full six confirmations. However, the public key can be calculated from the private key, so storing only the private key is also possible. Yesterday I login to my account after after bitmain antminer s9 watts bitmain antminer s7 batch 8 months. Nerd money! Use if you have a data cap or pay by the gigabyte. To Poloniex - are you planning to hold our money hostage? LevelDB is
will ripple rise offline bitcoin hardware wallet offline light-weight, single-purpose library for persistence with bindings to many platforms.
Many wallets focus on specific platforms or specific uses and some are more suitable for beginners while others are filled with features for advanced users. The response includes the reference to the transaction in which this unspent output is contained the payment from Joe and its value in satoshis, at 10 million, equivalent to 0. In the next sections we will demonstrate some very useful RPC commands and their expected output. Each miner includes a special transaction in his block, one that pays his own bitcoin address the block reward currently Later, as a professional, I developed my technical writing skills on the topic of data centers, writing for Network World magazine. Many volunteers also run bitcoin nodes on rented servers, usually some variant of Linux. Unlike other foreign currencies, you cannot yet buy bitcoin at a bank or foreign exchange kiosk. Exchanges of this kind should register with the SEC as a broker-dealer and become a member of a self-regulatory organization SRO. All previous releases of Cardano were scope-based, i. A full node handles all aspects of the protocol and can independently validate the entire blockchain and any transaction. The secret number that unlocks bitcoin sent to the corresponding address. The Open Assets Protocol is an evolution of the concept of colored coins. Users should be aware that once a bitcoin address is attached to an identity, all associated bitcoin transactions are also easy to identify and track. Here are some of the most popular:. Nguyen 1st edition and Will Binns 2nd edition , who worked tirelessly to curate, manage and resolve pull requests, issue reports, and perform bug fixes on GitHub. As you can see from the graph of the elliptic curve in [ecc-curve] , the curve is symmetric, meaning it is reflected like a mirror by the x-axis. Cryptocurrency exchanges would subsequently be governed by the same rules as traditional exchanges. These characters make it easy for humans to identify the type of data that is encoded and how to use it. A Micropayment Channel or Payment Channel is class of techniques designed to allow users to make multiple Bitcoin transactions without committing all of the transactions to the Bitcoin block chain. A service listing the market capitalization and exchange rates of hundreds of crypto-currencies, including bitcoin. Elliptic curve multiplication is a type of function that cryptographers call a "trap door" function:
 For comparison, the visible universe is estimated to contain 10 80 atoms. I repeatedly got stuck and a bit despondent as I struggled to make the topic easy to understand and create a narrative around such a dense technical subject. You can see the complete fee schedule. If you can use a programming language, this book will teach you how cryptographic currencies work, how to use them, and how to develop software that works with. You'll need to first buy bitcoin elsewhere, and then deposit it to be able to tade. Change to this directory by typing cd bitcoin at the prompt:. Some of the examples will require the use of Bitcoin Core, which, in addition to being a full client, also exposes APIs to the wallet, network, and transaction services. Cryptocurrency exchanges would subsequently be governed by the same rules as traditional exchanges. Why don't they bend the hose? In the US, the SEC has issued a public has anyone cashed our bitcoin miner android how to get your private keys from bitcoin core reaffirming registration and regulatory requirements for online platforms trading cryptocurrencies. The leafcutter ant is a species that exhibits highly complex behavior in a colony super-organism, but each individual ant operates on a set of simple rules driven by social interaction and the exchange of chemical scents pheromones. A blockchain explorer is a web application that operates as a bitcoin search engine, in that it allows you to search for addresses, chargeback transaction bitcoin coinbase cpu mining memory per thread, and blocks and see the relationships and flows between. Earn bitcoin by selling a product or service for bitcoin. I have never made trades on this account, and only seek to see what was left behind command prompt bitcoin calculator game litecoin blockchain download the early days of my mining. While an on-chain transaction - usually referred to as simply a transaction - modifies the blockchain and depends on the blockchain to determine its validity an off-chain transaction relies on other methods to record and validate the transaction. Offline storage is also often referred to as cold storage.
You may have heard that bitcoin is based on cryptography , which is a branch of mathematics used extensively in computer security. In bitcoin, miners must find a numeric solution to the SHA algorithm that meets a network-wide target, the difficulty target. The Hierarchical Deterministic HD key creation and transfer protocol BIP32 , which allows creating child keys from parent keys in a hierarchy. Additionally, it is recommended that you set up the alerting mechanism. The keys controlling bitcoin can also be printed for long-term storage. Eventually, I decided to tell the story of bitcoin through the stories of the people using bitcoin and the whole book became a lot easier to write. At its core, money simply facilitates the exchange of value between people. It is purposefully not Turing-complete, with no loops. Depending on whether you choose to index all transactions and keep a full copy of the blockchain, you may also need a lot of disk space and RAM. Tags Circle Exchange Poloniex. Next, we will look at how she buys bitcoin from her friend Joe and how Joe sends the bitcoin to her wallet. Bitcoin Core implements all aspects of bitcoin, including wallets, a transaction and block validation engine, and a full network node in the peer-to-peer bitcoin network. To comment or ask technical questions about this book, send email to bookquestions oreilly.
For comparison, the visible universe is estimated to contain 10 80 atoms. I repeatedly got stuck and a bit despondent as I struggled to make the topic easy to understand and create a narrative around such a dense technical subject. You can see the complete fee schedule. If you can use a programming language, this book will teach you how cryptographic currencies work, how to use them, and how to develop software that works with. You'll need to first buy bitcoin elsewhere, and then deposit it to be able to tade. Change to this directory by typing cd bitcoin at the prompt:. Some of the examples will require the use of Bitcoin Core, which, in addition to being a full client, also exposes APIs to the wallet, network, and transaction services. Cryptocurrency exchanges would subsequently be governed by the same rules as traditional exchanges. Why don't they bend the hose? In the US, the SEC has issued a public has anyone cashed our bitcoin miner android how to get your private keys from bitcoin core reaffirming registration and regulatory requirements for online platforms trading cryptocurrencies. The leafcutter ant is a species that exhibits highly complex behavior in a colony super-organism, but each individual ant operates on a set of simple rules driven by social interaction and the exchange of chemical scents pheromones. A blockchain explorer is a web application that operates as a bitcoin search engine, in that it allows you to search for addresses, chargeback transaction bitcoin coinbase cpu mining memory per thread, and blocks and see the relationships and flows between. Earn bitcoin by selling a product or service for bitcoin. I have never made trades on this account, and only seek to see what was left behind command prompt bitcoin calculator game litecoin blockchain download the early days of my mining. While an on-chain transaction - usually referred to as simply a transaction - modifies the blockchain and depends on the blockchain to determine its validity an off-chain transaction relies on other methods to record and validate the transaction. Offline storage is also often referred to as cold storage.
You may have heard that bitcoin is based on cryptography , which is a branch of mathematics used extensively in computer security. In bitcoin, miners must find a numeric solution to the SHA algorithm that meets a network-wide target, the difficulty target. The Hierarchical Deterministic HD key creation and transfer protocol BIP32 , which allows creating child keys from parent keys in a hierarchy. Additionally, it is recommended that you set up the alerting mechanism. The keys controlling bitcoin can also be printed for long-term storage. Eventually, I decided to tell the story of bitcoin through the stories of the people using bitcoin and the whole book became a lot easier to write. At its core, money simply facilitates the exchange of value between people. It is purposefully not Turing-complete, with no loops. Depending on whether you choose to index all transactions and keep a full copy of the blockchain, you may also need a lot of disk space and RAM. Tags Circle Exchange Poloniex. Next, we will look at how she buys bitcoin from her friend Joe and how Joe sends the bitcoin to her wallet. Bitcoin Core implements all aspects of bitcoin, including wallets, a transaction and block validation engine, and a full network node in the peer-to-peer bitcoin network. To comment or ask technical questions about this book, send email to bookquestions oreilly.

 Operation codes from the Bitcoin Script language which push data or perform functions within a pubkey script or signature script. Reducing this from the default will reduce your bandwidth consumption. It achieves this by catering to expert-level investors with significant holdings who Can You Divide A Bitcoin Gdax Exchange Litecoin To Bitcoin rather trade than let coins sit idle in their wallets. A network-wide setting that controls how much computation is required to produce a proof of work. While the Chinese government ordered banks to stop financing cryptocurrencies and processing payments for local cryptocurrency investors, the hype of Blockchain technology and cryptocurrency has not dematerialized. Whereas Coinbase receives about million, Poloniex 95 million and finally Kraken about 45 million monthly visits. In the next sections we will demonstrate some very useful RPC commands and their expected output. Set the minimum fee transaction you will relay. In the second edition, I again received a lot of help from many Bitcoin Core developers, including Eric Lombrozo who demystified Segregated Witness, Luke-Jr who helped improve the chapter on transactions, Johnson Lau who reviewed Segregated Witness and other chapters, and many others. If the result is less than n - 1 , we have a suitable private key. The following is a randomly generated private key k shown in hexadecimal format bits shown as 64 hexadecimal digits, each 4 bits:. Bitcoin represents the culmination of decades of research in cryptography and distributed systems and includes four key innovations brought together in a unique and powerful combination. These examples demonstrate how you might call the command. Do not write your own code to create a random number or use a "simple" random number generator offered by your programming language. As you can see, the first time you run bitcoind it tells you that you need to build a configuration file, with at least an rpcuser and rpcpassword entry. The resulting difference is the transaction fee that is collected by the miner as a fee for validating and including the transaction in a block to be recorded on the blockchain. In the next section we will examine the various configuration options and set up a configuration file. Information about Mastering Bitcoin as well as the Open Edition and translations are available on: Alice was introduced to bitcoin by a friend so she has an easy way to acquire her first bitcoin. A Hashlock is a type of encumbrance that restricts the spending of an output until a specified piece of data is publicly revealed. Gopesh has agreed to be paid in bitcoin. Rather, the useful property of asymmetric cryptography is the ability to generate digital signatures. This book represents the efforts and contributions of many people. Because the coinbase script can store between 2 and bytes of data, miners started using that space as extra nonce space, allowing them to explore a much larger range of block header values to find valid blocks. This is known as "transaction malleability," because transaction hashes can be modified prior to confirmation in a block. Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. Approximately 19 minutes later, a new block, , is mined by another miner. Anyone can contribute to the code—including you! The most important of these is the configure script that offers a number of different options to customize the build process.
The resulting transaction can be seen using a blockchain explorer web application, as shown in [transaction-alice]. That allows us to store only the x coordinate of the public key point, omitting the y coordinate and reducing the size of the key and the space required to store it by bits. If you are a US customer and if you make an ACH deposityour funds will immediately become available for trading. Despite these resource requirements, thousands of volunteers run bitcoin nodes. The private key must remain secret at all times, because revealing it to third parties is equivalent to giving them control over the bitcoin secured by that key. Imagine a giant sudoku puzzle, several thousand rows and columns in size. In most wallets, tapping the QR code will also magnify it, so that it can be how much electricity does bitcoin mining use bitcoin myhacks net scam easily scanned by a smartphone camera. The checksum is concatenated appended to the end. The scriptPubKey is also modified. To ask bitcoind to expose the private key, use the dumpprivkey command. I owe my love of words and books to my mother, Theresa, who raised me in a house with books lining every wall. Your money will be taken by another reader, or lost sell game keys for bitcoin unit price. With each transaction or block example, we will provide a URL so you can look it up yourself and study it in. Because the coinbase script can store between 2 and bytes of data, miners started using that space as extra nonce space, allowing them to explore a much larger range of block header values to what if i cant pay for bitcoins fastest pc bitcoin miner valid blocks. In some cases i.
Torsten Hartmann February 23, no comments. Alice is now ready bitcoin solutions ltd bitcoin core vs unlimited receive funds. Below it areblocks including block 0linked to each other in a chain of blocks blockchain all the way back to block 0, known as the genesis block. Alice places her order for a cup of coffee and Bob enters it into the register, as he does for all transactions. This book is here to help you get your job. Transactions like these are sometimes generated by wallet applications to clean up lots penshoppe ethereum philippines download ethereum walle3t smaller amounts that were received as change for payments. Poloniex forces new KYC policy on legacy account holders while failing to give prior notice. The most common form of transaction is a simple payment from one address to another, which often includes some "change" returned to the original owner. Bitcoin represents the culmination of decades of research in cryptography and distributed systems and includes four key innovations brought together in a unique and powerful combination. A common misconception about bitcoin transactions is that they must be "confirmed" by waiting 10 minutes for a new block, or up to 60 minutes for a full six confirmations. However, the public key can be calculated from the private key, so storing only the private key is also possible. Yesterday I login to my account after after bitmain antminer s9 watts bitmain antminer s7 batch 8 months. Nerd money! Use if you have a data cap or pay by the gigabyte. To Poloniex - are you planning to hold our money hostage? LevelDB is will ripple rise offline bitcoin hardware wallet offline light-weight, single-purpose library for persistence with bindings to many platforms.
Many wallets focus on specific platforms or specific uses and some are more suitable for beginners while others are filled with features for advanced users. The response includes the reference to the transaction in which this unspent output is contained the payment from Joe and its value in satoshis, at 10 million, equivalent to 0. In the next sections we will demonstrate some very useful RPC commands and their expected output. Each miner includes a special transaction in his block, one that pays his own bitcoin address the block reward currently Later, as a professional, I developed my technical writing skills on the topic of data centers, writing for Network World magazine. Many volunteers also run bitcoin nodes on rented servers, usually some variant of Linux. Unlike other foreign currencies, you cannot yet buy bitcoin at a bank or foreign exchange kiosk. Exchanges of this kind should register with the SEC as a broker-dealer and become a member of a self-regulatory organization SRO. All previous releases of Cardano were scope-based, i. A full node handles all aspects of the protocol and can independently validate the entire blockchain and any transaction. The secret number that unlocks bitcoin sent to the corresponding address. The Open Assets Protocol is an evolution of the concept of colored coins. Users should be aware that once a bitcoin address is attached to an identity, all associated bitcoin transactions are also easy to identify and track. Here are some of the most popular:. Nguyen 1st edition and Will Binns 2nd edition , who worked tirelessly to curate, manage and resolve pull requests, issue reports, and perform bug fixes on GitHub. As you can see from the graph of the elliptic curve in [ecc-curve] , the curve is symmetric, meaning it is reflected like a mirror by the x-axis. Cryptocurrency exchanges would subsequently be governed by the same rules as traditional exchanges. These characters make it easy for humans to identify the type of data that is encoded and how to use it. A Micropayment Channel or Payment Channel is class of techniques designed to allow users to make multiple Bitcoin transactions without committing all of the transactions to the Bitcoin block chain. A service listing the market capitalization and exchange rates of hundreds of crypto-currencies, including bitcoin. Elliptic curve multiplication is a type of function that cryptographers call a "trap door" function:
Operation codes from the Bitcoin Script language which push data or perform functions within a pubkey script or signature script. Reducing this from the default will reduce your bandwidth consumption. It achieves this by catering to expert-level investors with significant holdings who Can You Divide A Bitcoin Gdax Exchange Litecoin To Bitcoin rather trade than let coins sit idle in their wallets. A network-wide setting that controls how much computation is required to produce a proof of work. While the Chinese government ordered banks to stop financing cryptocurrencies and processing payments for local cryptocurrency investors, the hype of Blockchain technology and cryptocurrency has not dematerialized. Whereas Coinbase receives about million, Poloniex 95 million and finally Kraken about 45 million monthly visits. In the next sections we will demonstrate some very useful RPC commands and their expected output. Set the minimum fee transaction you will relay. In the second edition, I again received a lot of help from many Bitcoin Core developers, including Eric Lombrozo who demystified Segregated Witness, Luke-Jr who helped improve the chapter on transactions, Johnson Lau who reviewed Segregated Witness and other chapters, and many others. If the result is less than n - 1 , we have a suitable private key. The following is a randomly generated private key k shown in hexadecimal format bits shown as 64 hexadecimal digits, each 4 bits:. Bitcoin represents the culmination of decades of research in cryptography and distributed systems and includes four key innovations brought together in a unique and powerful combination. These examples demonstrate how you might call the command. Do not write your own code to create a random number or use a "simple" random number generator offered by your programming language. As you can see, the first time you run bitcoind it tells you that you need to build a configuration file, with at least an rpcuser and rpcpassword entry. The resulting difference is the transaction fee that is collected by the miner as a fee for validating and including the transaction in a block to be recorded on the blockchain. In the next section we will examine the various configuration options and set up a configuration file. Information about Mastering Bitcoin as well as the Open Edition and translations are available on: Alice was introduced to bitcoin by a friend so she has an easy way to acquire her first bitcoin. A Hashlock is a type of encumbrance that restricts the spending of an output until a specified piece of data is publicly revealed. Gopesh has agreed to be paid in bitcoin. Rather, the useful property of asymmetric cryptography is the ability to generate digital signatures. This book represents the efforts and contributions of many people. Because the coinbase script can store between 2 and bytes of data, miners started using that space as extra nonce space, allowing them to explore a much larger range of block header values to find valid blocks. This is known as "transaction malleability," because transaction hashes can be modified prior to confirmation in a block. Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. Approximately 19 minutes later, a new block, , is mined by another miner. Anyone can contribute to the code—including you! The most important of these is the configure script that offers a number of different options to customize the build process.
The resulting transaction can be seen using a blockchain explorer web application, as shown in [transaction-alice]. That allows us to store only the x coordinate of the public key point, omitting the y coordinate and reducing the size of the key and the space required to store it by bits. If you are a US customer and if you make an ACH deposityour funds will immediately become available for trading. Despite these resource requirements, thousands of volunteers run bitcoin nodes. The private key must remain secret at all times, because revealing it to third parties is equivalent to giving them control over the bitcoin secured by that key. Imagine a giant sudoku puzzle, several thousand rows and columns in size. In most wallets, tapping the QR code will also magnify it, so that it can be how much electricity does bitcoin mining use bitcoin myhacks net scam easily scanned by a smartphone camera. The checksum is concatenated appended to the end. The scriptPubKey is also modified. To ask bitcoind to expose the private key, use the dumpprivkey command. I owe my love of words and books to my mother, Theresa, who raised me in a house with books lining every wall. Your money will be taken by another reader, or lost sell game keys for bitcoin unit price. With each transaction or block example, we will provide a URL so you can look it up yourself and study it in. Because the coinbase script can store between 2 and bytes of data, miners started using that space as extra nonce space, allowing them to explore a much larger range of block header values to what if i cant pay for bitcoins fastest pc bitcoin miner valid blocks. In some cases i.
Torsten Hartmann February 23, no comments. Alice is now ready bitcoin solutions ltd bitcoin core vs unlimited receive funds. Below it areblocks including block 0linked to each other in a chain of blocks blockchain all the way back to block 0, known as the genesis block. Alice places her order for a cup of coffee and Bob enters it into the register, as he does for all transactions. This book is here to help you get your job. Transactions like these are sometimes generated by wallet applications to clean up lots penshoppe ethereum philippines download ethereum walle3t smaller amounts that were received as change for payments. Poloniex forces new KYC policy on legacy account holders while failing to give prior notice. The most common form of transaction is a simple payment from one address to another, which often includes some "change" returned to the original owner. Bitcoin represents the culmination of decades of research in cryptography and distributed systems and includes four key innovations brought together in a unique and powerful combination. A common misconception about bitcoin transactions is that they must be "confirmed" by waiting 10 minutes for a new block, or up to 60 minutes for a full six confirmations. However, the public key can be calculated from the private key, so storing only the private key is also possible. Yesterday I login to my account after after bitmain antminer s9 watts bitmain antminer s7 batch 8 months. Nerd money! Use if you have a data cap or pay by the gigabyte. To Poloniex - are you planning to hold our money hostage? LevelDB is will ripple rise offline bitcoin hardware wallet offline light-weight, single-purpose library for persistence with bindings to many platforms.
Many wallets focus on specific platforms or specific uses and some are more suitable for beginners while others are filled with features for advanced users. The response includes the reference to the transaction in which this unspent output is contained the payment from Joe and its value in satoshis, at 10 million, equivalent to 0. In the next sections we will demonstrate some very useful RPC commands and their expected output. Each miner includes a special transaction in his block, one that pays his own bitcoin address the block reward currently Later, as a professional, I developed my technical writing skills on the topic of data centers, writing for Network World magazine. Many volunteers also run bitcoin nodes on rented servers, usually some variant of Linux. Unlike other foreign currencies, you cannot yet buy bitcoin at a bank or foreign exchange kiosk. Exchanges of this kind should register with the SEC as a broker-dealer and become a member of a self-regulatory organization SRO. All previous releases of Cardano were scope-based, i. A full node handles all aspects of the protocol and can independently validate the entire blockchain and any transaction. The secret number that unlocks bitcoin sent to the corresponding address. The Open Assets Protocol is an evolution of the concept of colored coins. Users should be aware that once a bitcoin address is attached to an identity, all associated bitcoin transactions are also easy to identify and track. Here are some of the most popular:. Nguyen 1st edition and Will Binns 2nd edition , who worked tirelessly to curate, manage and resolve pull requests, issue reports, and perform bug fixes on GitHub. As you can see from the graph of the elliptic curve in [ecc-curve] , the curve is symmetric, meaning it is reflected like a mirror by the x-axis. Cryptocurrency exchanges would subsequently be governed by the same rules as traditional exchanges. These characters make it easy for humans to identify the type of data that is encoded and how to use it. A Micropayment Channel or Payment Channel is class of techniques designed to allow users to make multiple Bitcoin transactions without committing all of the transactions to the Bitcoin block chain. A service listing the market capitalization and exchange rates of hundreds of crypto-currencies, including bitcoin. Elliptic curve multiplication is a type of function that cryptographers call a "trap door" function:
