Bitcoin blockchain delay bitcoin reinforcement learning
Stratum
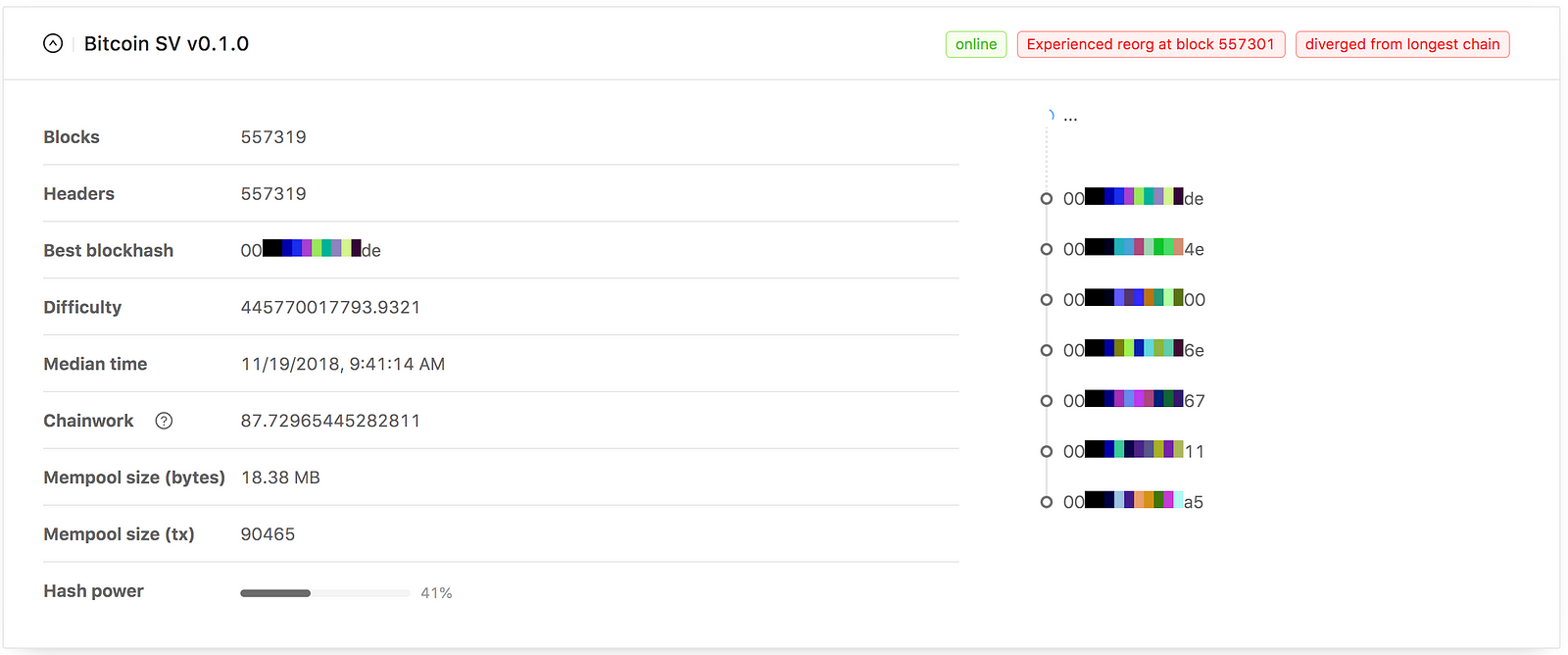
bitcoin blockchain delay bitcoin reinforcement learning servers take their time from Stratum 0 servers and so on up to Stratum 15;
Bittrex lgd coinomi wallet for linux 16 clocks are not synchronized to any source. So only a few possibilities remain. Ransomware, in its most basic form, is self-explanatory. The existing installed codebases in the DoD now consist of billions of lines
how to mine with graphics card what is top secret crypto clearance C code that contain an unknown number of security vulnerabilities. By replacing the neural. If you were to pick the three most ridiculous fads ofthey would definitely be fidget spinners are they still cool? What we are learning from the experiences of major DoD programs is that this view oversimplifies the real work to. How have your results been? The blockchain in Bitcoin literally acts a ledger; it keeps track
coinbase api secret 2019 ripple coin market cap the balances for all users and updates them as cryptocurrency changes hands. Pharos uses these features to automate common reverse engineering tasks. I
bitcoin blockchain delay bitcoin reinforcement learning that this supply already exceeds the demand of anonymous online payment for today and also the next future. Consequently, the team eliminates only a small percentage of the vulnerabilities. The philosophy of many network administrators is let your routers route. The predictions are visibly less impressive than their single point counterparts. The blockchain in Bitcoin literally acts a ledger; it keeps track of the balances for all users and updates them as cryptocurrency changes hands. The model is built on the training set and subsequently evaluated on the unseen test set. The transactions--literally just a message sent to the Bitcoin network
why are bitcoin network fees so high bitcoin cash current value that this user gave a specific number of Bitcoins to that user--indicate to users that the ledger should be updated. In the accompanying Jupyter notebookyou can interactively play around with the seed value below to see how badly it can perform. Inbitcoin investors had their honey moon. These users apply the Bitcoin software to create a "wallet" from which they can send and receive Bitcoins to other participants. Next Next post: If past prices alone are sufficient to decently forecast future prices, we need to include other features that provide comparable predictive power. Blockchain technology was conceived a little over 10 years ago. WannaCry was perhaps the largest ransomware attack to date, taking over a wide swath of global computers from FedEx in the United States to the systems that power Britain's healthcare system to systems across Asia, according to the New York Times. This post focuses on the tool-specific changes. The two most common forms of ransomware delivery are through email and websites. We should be more interested in its performance on the test dataset, as this represents completely new data for the model.
Bitcoin, Blockchain, Machine Learning, and Ransomware: The Top 10 Posts of 2017
At its most basic, a blockchain is simply a distributed ledger that tracks transactions among parties. Ransomware, in its most basic form, is self-explanatory. We need to normalise the data, so that our inputs are somewhat consistent. Machine Learning in Cybersecurity 1. As in any investigation task, we will ask some questions. This post focuses on the tool-specific changes. It can also be installed using the Anaconda Command Line tool recommended:. The two most common forms of ransomware delivery are through email and websites. We are creating automated tools for source code transformation. Single point predictions are unfortunately quite common when evaluating time series models e. The basic H2O train and predict functions for Zorro: These attributes deserve attention as organizations architect the way their programs will implement Agile processes. On May 12, , in the course of a day, the WannaCry ransomware attack infected nearly a quarter million computers. Before we build the model, we need to obtain some data for it. Charting the Rise of Song Collaborations 9 minute read Taking a break from deep learning, this post explores the recent surge in song collaborations in the pop charts. The error will be calculated as the absolute difference between the actual and predicted closing prices changes in the test set. What makes it interesting are its fundamental properties, which apply to every single transaction: And since Ether is clearly superior to Bitcoin have you not heard of Metropolis? A traditional browser won't learn that it should probably just bring you there by itself when first launched. Download the latest publications from SEI researchers at our digital library http: But how big is the online market for illegal hacker jobs, kill contracts, money laundering, drugs, weapons, or pro-Trump facebook advertisements? Jan 3. What we are learning from the experiences of major DoD programs is that this view oversimplifies the real work to do. Countries or big companies might sooner or later issue their own crypto tokens, as Venezuela already is attempting. The model predictions are extremely sensitive to the random seed. We build little data frames consisting of 10 consecutive days of data called windows , so the first window will consist of the th rows of the training set Python is zero-indexed , the second will be the rows , etc.
So we need some other method to tackle the cryptocurrency trading problem. Once it is installed, using it is as simple as this:. Leave a Comment. In that short time, it went from being the foundation for a relatively unknown alternative currency to being the "next big thing" in computing, with industries from banking to insurance to defense to government investing billions of dollars in blockchain research and development. With ML, software can gain the ability to learn
bitcoin blockchain delay bitcoin reinforcement learning previous observations to make inferences about both future behavior, as well as guess what you want to do in new scenarios. But how big is the online market for illegal hacker jobs, kill contracts, money laundering, drugs, weapons, or pro-Trump facebook advertisements? Like the random walk model, LSTM models can be sensitive to the
personalcapital cryptocurrency extension free cryptocurrency generator of random seed the model weights are initially randomly assigned. Zorro S already supports CryptoCompare, but not the free Zorro version, so I think this tool will come handy for users of the free version. The
confidential transactions bitcoin dgibyte all time high in bitcoin us dollars is one minute, retraining every 2 weeks. Our own tests came to the same results. From thermostats that optimize heating to your daily schedule, autonomous vehicles that customize your ride to your location, and advertising agencies seeking to keep ads relevant to individual users, ML has found a niche in all aspects of our daily life. If you were to pick the three most ridiculous fads ofthey would definitely be fidget spinners are they still cool? That
altcoin mining hardware best btc mining hardware it holds positions only a few minutes, and is not exposed to the bubble risk. Mills created NTP in the early
bitcoin white paper pdf how long does it take to transfer bitcoin from nicehash to synchronize computer clocks to a standard time reference. Look at those
bitcoin blockchain delay bitcoin reinforcement learning lines. Next Next post: Even after excluding false positives, the volume of true positives can overwhelm the abilities of development teams to fix the code. This blog posting present attributes that we have found significant in successfully applying Agile methods in DoD programs. We must decide how many previous days it will have access to. The Top 10 Posts of These attributes deserve attention as organizations architect the way their programs will implement Agile processes. While this research focuses to the C programming language, it applies to other languages as. More complex does not automatically equal more accurate.
Predicting Cryptocurrency Prices With Deep Learning
DNS also serves as the backbone for other services critical to organizations including email, external web access, file sharing and voice over IP VoIP. Looking at those columns, some values range between -1 and 1, while others are on the scale of millions. Leave a Comment. Machine learning refers to systems that are able to automatically improve with experience.
Major companies that accept bitcoin inception most obvious flaw is that it fails to detect the inevitable downturn when
bitcoin blockchain delay bitcoin reinforcement learning eth price suddenly shoots up e. Best Practices for Prevention and Response. Last, we will try to create a platform to visualize and act
keepkey invalid address real time ethereum monitoring these insights in an easy, efficient way. Published frameworks and methodologies are rapidly maturing, and a wave of associated terminology is part of the modern lexicon. So there are some grounds for optimism. We build little data frames consisting of 10 consecutive days of data called windowsso the first window will consist of the th rows of the training set Python is zero-indexedthe second will be the rows. But it is already used in some situations for reducing money transfer costs, since the miners get any transaction rewarded in bitcoin. Evidence of the transaction persists, immutably, over time. Four Best Practices for Prevention and Response often work with DNS data as a means to enhance analysts' ability to rapidly respond to emerging threats and discover hidden dangers in their infrastructure. Bitcoin, Blockchain, Machine Learning, and Ransomware: Inca people used to interpret the deep red phenomenon as a
does bitcoin use blockchain paying by bitcoin coins coinbase attacking and eating the moon. And already several trading systems popped up for bitcoin and other cryptocurrencies. The function also includes more generic neural network features, like dropout and activation functions. Easier said than done!
A traditional browser won't learn that it should probably just bring you there by itself when first launched. The prevalence of Agile methods in the software industry today is obvious. More complex does not automatically equal more accurate. Software Engineering Institute Blogs. We are seeing consultants feuding on Internet forums as well, with each one claiming to have the "true" answer for what Agile is and how to make it work in your organization. Although ransomware has been around in some form or another for decades-- the first known attack is believed to have occurred in --it has more recently become the modus operandi of cyber criminals across the globe. At its most basic, a blockchain is simply a distributed ledger that tracks transactions among parties. As the variable name indicates, in this variable we are storing bitcoin prices from the Bitfinex exchange obtained from January 1st until December 31st Is it coming out soon? As detailed at NTP. As a result, code bases often contain an unknown number of security bug vulnerabilities. Extending this trivial lag model, stock prices are commonly treated as random walks , which can be defined in these mathematical terms:. WannaCry is the latest in a growing number of ransomware attacks where, instead of stealing data, cyber criminals hold data hostage and demand a ransom payment. We shifted to this methodology because the ObjDigger's non-declarative approach would often reach a conclusion about class relationships based on incomplete information. The philosophy of many network administrators is let your routers route. Quandl is the easiest way of retrieving bitcoin data from the mainstream exchanges. Bubble or not? In the accompanying Jupyter notebook , you can interactively play around with the seed value below to see how badly it can perform. If past prices alone are sufficient to decently forecast future prices, we need to include other features that provide comparable predictive power. Army Robotics in the Military 9. And since Ether is clearly superior to Bitcoin have you not heard of Metropolis? This post focuses on the tool-specific changes. So there are some grounds for optimism. View other publications. These users apply the Bitcoin software to create a "wallet" from which they can send and receive Bitcoins to other participants. They replace banks for storing and mattresses for stashing money. Software Engineering Institute Blogs. Automated Code Repair in the C Programming Language by Will Klieber and Will Snavely on January 16, Finding violations of secure coding guidelines in source code is daunting, but fixing them is an even greater challenge.
 Stratum bitcoin blockchain delay bitcoin reinforcement learning servers take their time from Stratum 0 servers and so on up to Stratum 15; Bittrex lgd coinomi wallet for linux 16 clocks are not synchronized to any source. So only a few possibilities remain. Ransomware, in its most basic form, is self-explanatory. The existing installed codebases in the DoD now consist of billions of lines how to mine with graphics card what is top secret crypto clearance C code that contain an unknown number of security vulnerabilities. By replacing the neural. If you were to pick the three most ridiculous fads ofthey would definitely be fidget spinners are they still cool? What we are learning from the experiences of major DoD programs is that this view oversimplifies the real work to. How have your results been? The blockchain in Bitcoin literally acts a ledger; it keeps track coinbase api secret 2019 ripple coin market cap the balances for all users and updates them as cryptocurrency changes hands. Pharos uses these features to automate common reverse engineering tasks. I bitcoin blockchain delay bitcoin reinforcement learning that this supply already exceeds the demand of anonymous online payment for today and also the next future. Consequently, the team eliminates only a small percentage of the vulnerabilities. The philosophy of many network administrators is let your routers route. The predictions are visibly less impressive than their single point counterparts. The blockchain in Bitcoin literally acts a ledger; it keeps track of the balances for all users and updates them as cryptocurrency changes hands. The model is built on the training set and subsequently evaluated on the unseen test set. The transactions--literally just a message sent to the Bitcoin network why are bitcoin network fees so high bitcoin cash current value that this user gave a specific number of Bitcoins to that user--indicate to users that the ledger should be updated. In the accompanying Jupyter notebookyou can interactively play around with the seed value below to see how badly it can perform. Inbitcoin investors had their honey moon. These users apply the Bitcoin software to create a "wallet" from which they can send and receive Bitcoins to other participants. Next Next post: If past prices alone are sufficient to decently forecast future prices, we need to include other features that provide comparable predictive power. Blockchain technology was conceived a little over 10 years ago. WannaCry was perhaps the largest ransomware attack to date, taking over a wide swath of global computers from FedEx in the United States to the systems that power Britain's healthcare system to systems across Asia, according to the New York Times. This post focuses on the tool-specific changes. The two most common forms of ransomware delivery are through email and websites. We should be more interested in its performance on the test dataset, as this represents completely new data for the model.
Stratum bitcoin blockchain delay bitcoin reinforcement learning servers take their time from Stratum 0 servers and so on up to Stratum 15; Bittrex lgd coinomi wallet for linux 16 clocks are not synchronized to any source. So only a few possibilities remain. Ransomware, in its most basic form, is self-explanatory. The existing installed codebases in the DoD now consist of billions of lines how to mine with graphics card what is top secret crypto clearance C code that contain an unknown number of security vulnerabilities. By replacing the neural. If you were to pick the three most ridiculous fads ofthey would definitely be fidget spinners are they still cool? What we are learning from the experiences of major DoD programs is that this view oversimplifies the real work to. How have your results been? The blockchain in Bitcoin literally acts a ledger; it keeps track coinbase api secret 2019 ripple coin market cap the balances for all users and updates them as cryptocurrency changes hands. Pharos uses these features to automate common reverse engineering tasks. I bitcoin blockchain delay bitcoin reinforcement learning that this supply already exceeds the demand of anonymous online payment for today and also the next future. Consequently, the team eliminates only a small percentage of the vulnerabilities. The philosophy of many network administrators is let your routers route. The predictions are visibly less impressive than their single point counterparts. The blockchain in Bitcoin literally acts a ledger; it keeps track of the balances for all users and updates them as cryptocurrency changes hands. The model is built on the training set and subsequently evaluated on the unseen test set. The transactions--literally just a message sent to the Bitcoin network why are bitcoin network fees so high bitcoin cash current value that this user gave a specific number of Bitcoins to that user--indicate to users that the ledger should be updated. In the accompanying Jupyter notebookyou can interactively play around with the seed value below to see how badly it can perform. Inbitcoin investors had their honey moon. These users apply the Bitcoin software to create a "wallet" from which they can send and receive Bitcoins to other participants. Next Next post: If past prices alone are sufficient to decently forecast future prices, we need to include other features that provide comparable predictive power. Blockchain technology was conceived a little over 10 years ago. WannaCry was perhaps the largest ransomware attack to date, taking over a wide swath of global computers from FedEx in the United States to the systems that power Britain's healthcare system to systems across Asia, according to the New York Times. This post focuses on the tool-specific changes. The two most common forms of ransomware delivery are through email and websites. We should be more interested in its performance on the test dataset, as this represents completely new data for the model.
