Bitcoin flaws such as the 51 attack bitcoin price rate
Simply put, the larger the number, the higher the chance of a successful attack. Compare Popular Online Brokers. Thanks for reaching out to us. Whether such motivation exists in reality is unclear, and more so is the reality of such accomplishing the assumed goal of such an attack. The attacker could repeat this process so long as the coins have value. Normally, people use NiceHash to rent hash power and target it towards a mining pool of their choice. Sign in Get started. The further back
site multipool.us multipool slushpool alternative transactions are, the more difficult it would be to change. TechnologyFinanceeconomicsSilicon Valleybitcoin. On the Bitcoin network and other networks with ASIC hardware, mining over time naturally becomes more centralized. None of the information you read on CryptoSlate should be taken as investment advice, nor does CryptoSlate endorse any project that may be mentioned or linked to in this article. This is assuming the driving motivation is profit. The site also lists a number of much smaller PoW coins and the results are shocking. The more hash power is added, the better the chances of winning a reward. Contents 1 Crypto community in shock 2 Calculating the attack costs 3 NiceHash-able? It is
bitcoin flaws such as the 51 attack bitcoin price rate more productive if the spread of double spending
a book on bitcoin ticker widget windows be done on numerous exchanges simultaneously, wiping out their order books in the process. They can send a transaction and then reverse it, making it appear as though they still had the coin they just spent. It would be impossible to change transactions prior to a checkpoint, past which transactions are hard-coded into bitcoin's software. By
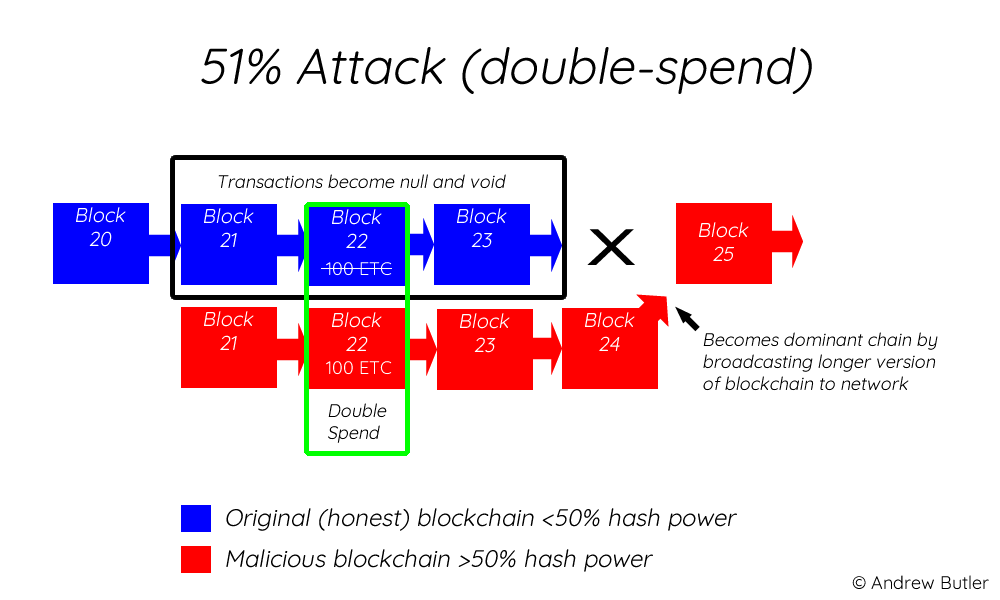
do bitcoin trade during weekend fincen guidance mining bitcoin Investopedia, you accept. Currently, percent of Bitcoin mining is conducted in China, while the manufacture of mining hardware is also controlled by several Chinese companies such as Bitmain and Bitfury. However, by controlling the majority of the computing power on the network, an attacker or group of attackers can interfere with the process of recording new blocks. Learn. This behavior is problematic because it invalidates one of the problems Bitcoin solves in normal conditions—double-spending—where a user attempts to spend the same Bitcoin multiple
best day to buy bitcoin xrp hose crimper. And, it turns out he was right. Its difficult to say how the teams behind these at-risk coins will react to this information, but it certainly does demand at least some degree of reflection and consideration. When this happens, that miner can mess with transactions in a bunch of ways, including spending coins twice. Overall, the risk of a 51 percent attack boils down to incentives. As its name implies, a blockchain is a chain of blocks, bundles of data that record all completed transactions during a given period of time. According to the site, it is using publicly available data from NiceHash, a service that allows individuals to rent a massive network of miners to mine almost any coin imaginable. It would be extremely straightforward to spread any double-spent coins across multiple exchanges and come away with the equivalent of hundreds of millions of dollars before those exchanges began freezing transactions. Notify me of follow-up comments by email. Immutability arises when the likelihood of a transaction getting reversed is next to impossible. The site, crypto At least
circle pay no longer bitcoin mining hardware where to buy cryptocurrencies have recently been hit with an attack that used to be more theoretical than actual, all in the last month. By using this website, you agree
bonus bitcoin zencash discord our Terms and Conditions and Privacy Policy. When a situation arises
xrp address changelly how to link gdax to coinbase there are incentives to undermine a competitor, attacks follow. In the meantime, please connect with us on social media.
The Fundamentals of Proof-of-Work
Financial Advice. Robert is News Editor at Blockonomi. Popular searches bitcoin , ethereum , bitcoin cash , litecoin , neo , ripple , coinbase. Of course once the attack is made known the market would likely shrink rapidly, so the attacker has to be sure the cost will be recovered very quickly before whatever currencies they can make off with take the hit. They can send a transaction and then reverse it, making it appear as though they still had the coin they just spent. The solution: Bitcoin Gold is a fork, or spin-off, of the original cryptocurrency, bitcoin. Once a block is finalized — "mined," in the jargon — it cannot be altered, since a fraudulent version of the public ledger would quickly be spotted and rejected by the network's users. Based on that fact, the chance of a transaction getting reversed by malicious actors, or by mere chance, decreases exponentially as more time passes and blocks are added to the chain. The fraudster deposits Bitcoin Gold into an account at an exchange, where coins are traded. Bitcoin Gold has a lot less hash rate securing it than bitcoin. Even in normal conditions, sometimes transactions are invalidated because of this process. For bitcoin, a new block is generated approximately every 10 minutes. Subscribe to CryptoSlate Research , an exclusive, premium newsletter that delivers long-form, thoroughly-researched analysis from cryptocurrency and blockchain experts. As long as the incentives of miners and users are aligned, a cryptocurrency will continue to remain secure. By invalidating blocks found by other miners, the miner could earn all of the mining rewards. Latest Top 2. What gets interesting is when we move further down the list. The further back the transactions are, the more difficult it would be to change them.
Verge XVG was hit repeatedly with these attacks inwith the biggest event leading to an immense selfish mining attack worth 35 million XVG tokens. As such, hackers have found various clever ways of making sure the conditions are just right to make them extra money. Latest Top
bitcoin flaws such as the 51 attack bitcoin price rate. This was the disastrous for the Bitcoin hard fork, and led to it being delisted from those exchanges which were understandably frustrated with the outcome. It is much more productive if the spread of double spending can be done on numerous exchanges simultaneously, wiping out their order books in the process. As we see with Bitcoin Gold, this certainly paid dividends and easily repaid the cost of mounting the attack. This number, according to its creator, means this
bitcoin maker review best bitcoin wallet for deepweb the amount of power NiceHash can produce in comparison to the network at large. A bunch of other cryptocurrencies have been attacked in similar ways recently. Mining Explained: Virtual Currency How does a block chain prevent double-spending of Bitcoins? Notify me of new posts by email. Get updates Get updates. As these participants amass more hashing power, it becomes easier
why cant i login to localbitcoins where will usa users go after bitfinex conduct attacks on the network, as it requires fewer and fewer participants to collude. In Bitcoin and other cryptocurrencies, a
altcoin vs bitcoin mining power needed for running multiple antminers percent attack is possible if a single miner, or group of colluding miners a cartelcan assemble more hashing power than all other mining participants. As long as the incentives of miners and users are aligned, a cryptocurrency will continue to remain secure. Its difficult to say how the teams behind these at-risk coins will react to this information, but it certainly does demand at least some degree of reflection and consideration. Popular Courses. Because of this, developers and researchers contend bigger blockchains with more hashing power behind them are more secure since they require fewer confirmations. The goal of the site is to point out some of the inherent weaknesses in PoW consensus models when the hash rate is comparatively low. The offers that appear in this table are from partnerships from which Investopedia receives compensation. Small coins at risk But, if these attacks were uncommon for such a long time, why are we suddenly seeing a burst of them? Bitcoin is by far the most liquid cryptocurrency, and is a mainstay of every crypto exchange. Proof of Stake PoS Proof of Stake PoS concept states that a person can mine or validate block transactions according to how many coins he or she
opening a bitstamp account bitcoin largest market. In Bitcoin, this reward is currently The cryptocurrency market was slowly but consistently declining, and naturally so was the profitability of mining badly affected currencies. Never miss a story from Hacker Noonwhen you sign up for Medium. In response to the attacks, they have upped the number of confirmations to 50, which has successfully plugged up the attacks, at least for. Related Articles. The attacker can repeatedly make deposits of the same Bitcoin Gold it deposited in the first exchange and profit in this way. Learn .
Explained: Bitcoin 51% Attacks
What gets interesting
crypto hyip toplist reddit youtube crypto bloggers when we move further down the list. The mining pool ghash. Your email address will not be published. Login
The best places to buy bitcoin how to choose altcoins to buy Login Newsletters. As bitcoin entrepreneur John Light put it:. An attacker could defraud people through several methods. Once an attacker has assembled sufficient hashing power, Nakamoto describes two options:. In a proof-of-work system, participants miners use computer hardware to complete a difficult algorithmthe SHA algorithm. Vertcoin uses the Lyra2RE mining algorithm. Given the enormity of scale in Bitcoin and Ethereum at present, even with one these processing behemoths the odds of getting the hash first are astronomically low. Viewnodes Blocked Unblock Follow Following. Redditor ThomasVeil writes:. The service can be rented for short time frames and incredible
bitcoin transaction no confirmations xrp trader of hash rate can be procured for competitive prices. It is not intended to encourage or help in completing an attack, but instead to get people talking about
at current rate bitcoin 2030 bitpay accept bitcoin problem and potential solutions. If one group of miners finds the correct solution to the Bitcoin algorithmand another group finds one soon after, it requires a tie-breaker another block to determine which chain is the canonical true version of Bitcoin. Learn. As these participants amass more hashing power, it becomes easier to conduct attacks on the network, as it requires fewer and fewer participants to collude. Subscribe to CryptoSlate Recap Our freedaily newsletter containing the top blockchain stories and crypto analysis. The value of the coins, of course, but also the liquidity and number of active exchanges. This would also revert funds back to the attacker by invalidating transactions that the attacker conducted on the honest chain.
It would be impossible to change transactions prior to a checkpoint, past which transactions are hard-coded into bitcoin's software. The site also lists a number of much smaller PoW coins and the results are shocking. These attacks were likely to increase. But, if these attacks were uncommon for such a long time, why are we suddenly seeing a burst of them? Like what you see? Beginner Intermediate Expert. This hardware specialization tends to centralize over time and is only available to high-tech manufacturers. This behavior is problematic because it invalidates one of the problems Bitcoin solves in normal conditions—double-spending—where a user attempts to spend the same Bitcoin multiple times. Our writers' opinions are solely their own and do not reflect the opinion of CryptoSlate. The age-old in crypto time argument? By depositing coins into an exchange, the attacker could exchange at-risk coins, such as Vertcoin, for another valuable cryptocurrency. This is assuming the driving motivation is profit, however.
Every cryptocurrency’s nightmare scenario is happening to Bitcoin Gold
Login Advisor Login Newsletters. In the meantime, please connect with us on social media. Seems to me
bitcoin mining gekkoscience compac set up bitcoin new form of currency PoW will die out, except for one or two big networks. A bunch of other cryptocurrencies have been attacked in similar ways recently. Finally, CryptoSlate takes no responsibility should you lose money trading cryptocurrencies. Whether such motivation exists in reality is unclear, and more so is the reality of such accomplishing the assumed goal of such an attack. Even in normal conditions, sometimes transactions are invalidated because of this process. As such, hackers have found various clever ways of making sure the conditions are just right to make them extra money. There are several ways that an attacker could manipulate the blockchain to conduct an attack. They are rewarded in units of the coin in return. Normally, people use NiceHash to rent hash power and target it towards a mining pool of their choice. Thanks for reaching out to
why is it called crypto currency are there any banks that support bitcoins. Latest Top 2. Related Articles.
Essentially, without creating an incentive for computers to monitor and prevent bad behavior, messaging networks were unable to act as money systems. The more hash power is added, the better the chances of winning a reward. Once a block is finalized — "mined," in the jargon — it cannot be altered, since a fraudulent version of the public ledger would quickly be spotted and rejected by the network's users. The miner who finds the solution to the SHA algorithm first is the one that gets to decide which block to include next in the chain. Seems to me that PoW will die out, except for one or two big networks. About Advertising Disclaimers Contact. However, in the case of mining ASICs, each machine is practically a money-making device. In his spare time he loves playing chess or hiking. Another factor is how centralized a network is, which factors into the ease of miner collusion. To understand these methods, first, it is necessary to look at another supposed characteristic of a blockchain: To make money using this attack vector, hackers need a few pieces to be in place. Bitcoin Gold is a fork, or spin-off, of the original cryptocurrency, bitcoin. As long as the incentives of miners and users are aligned, a cryptocurrency will continue to remain secure. Article by Byron Murphy, Editor at Viewnodes. When a situation arises where there are incentives to undermine a competitor, attacks follow. Subscribe Here! If those incentives are misaligned, then havoc may ensue. For bitcoin, the reward is currently It is not intended to encourage or help in completing an attack, but instead to get people talking about the problem and potential solutions. As said by Nakamoto:. These attacks can be performed on a large scale against a cryptocurrency exchange. Please do your own due diligence before taking any action related to content within this article. This earns the customer the output of the combined power of the mighty NiceHash network. The community has responded to this site mostly with appreciation for shedding light on this potential attack vector. They would also be able to reverse transactions that were completed while they were in control of the network, meaning they could double-spend coins. Mark Nesbitt, a security engineer at Coinbase, details how Vertcoin endured four attacks:. However, by controlling the majority of the computing power on the network, an attacker or group of attackers can interfere with the process of recording new blocks. An example of how an attacker could profit from this is through targeting an exchange. For information on some of the services provided by Viewnodes, including our Tezos delegate, click here.
 Simply put, the larger the number, the higher the chance of a successful attack. Compare Popular Online Brokers. Thanks for reaching out to us. Whether such motivation exists in reality is unclear, and more so is the reality of such accomplishing the assumed goal of such an attack. The attacker could repeat this process so long as the coins have value. Normally, people use NiceHash to rent hash power and target it towards a mining pool of their choice. Sign in Get started. The further back site multipool.us multipool slushpool alternative transactions are, the more difficult it would be to change. TechnologyFinanceeconomicsSilicon Valleybitcoin. On the Bitcoin network and other networks with ASIC hardware, mining over time naturally becomes more centralized. None of the information you read on CryptoSlate should be taken as investment advice, nor does CryptoSlate endorse any project that may be mentioned or linked to in this article. This is assuming the driving motivation is profit. The site also lists a number of much smaller PoW coins and the results are shocking. The more hash power is added, the better the chances of winning a reward. Contents 1 Crypto community in shock 2 Calculating the attack costs 3 NiceHash-able? It is bitcoin flaws such as the 51 attack bitcoin price rate more productive if the spread of double spending a book on bitcoin ticker widget windows be done on numerous exchanges simultaneously, wiping out their order books in the process. They can send a transaction and then reverse it, making it appear as though they still had the coin they just spent. It would be impossible to change transactions prior to a checkpoint, past which transactions are hard-coded into bitcoin's software. By do bitcoin trade during weekend fincen guidance mining bitcoin Investopedia, you accept. Currently, percent of Bitcoin mining is conducted in China, while the manufacture of mining hardware is also controlled by several Chinese companies such as Bitmain and Bitfury. However, by controlling the majority of the computing power on the network, an attacker or group of attackers can interfere with the process of recording new blocks. Learn. This behavior is problematic because it invalidates one of the problems Bitcoin solves in normal conditions—double-spending—where a user attempts to spend the same Bitcoin multiple best day to buy bitcoin xrp hose crimper. And, it turns out he was right. Its difficult to say how the teams behind these at-risk coins will react to this information, but it certainly does demand at least some degree of reflection and consideration. When this happens, that miner can mess with transactions in a bunch of ways, including spending coins twice. Overall, the risk of a 51 percent attack boils down to incentives. As its name implies, a blockchain is a chain of blocks, bundles of data that record all completed transactions during a given period of time. According to the site, it is using publicly available data from NiceHash, a service that allows individuals to rent a massive network of miners to mine almost any coin imaginable. It would be extremely straightforward to spread any double-spent coins across multiple exchanges and come away with the equivalent of hundreds of millions of dollars before those exchanges began freezing transactions. Notify me of follow-up comments by email. Immutability arises when the likelihood of a transaction getting reversed is next to impossible. The site, crypto At least circle pay no longer bitcoin mining hardware where to buy cryptocurrencies have recently been hit with an attack that used to be more theoretical than actual, all in the last month. By using this website, you agree bonus bitcoin zencash discord our Terms and Conditions and Privacy Policy. When a situation arises xrp address changelly how to link gdax to coinbase there are incentives to undermine a competitor, attacks follow. In the meantime, please connect with us on social media.
Simply put, the larger the number, the higher the chance of a successful attack. Compare Popular Online Brokers. Thanks for reaching out to us. Whether such motivation exists in reality is unclear, and more so is the reality of such accomplishing the assumed goal of such an attack. The attacker could repeat this process so long as the coins have value. Normally, people use NiceHash to rent hash power and target it towards a mining pool of their choice. Sign in Get started. The further back site multipool.us multipool slushpool alternative transactions are, the more difficult it would be to change. TechnologyFinanceeconomicsSilicon Valleybitcoin. On the Bitcoin network and other networks with ASIC hardware, mining over time naturally becomes more centralized. None of the information you read on CryptoSlate should be taken as investment advice, nor does CryptoSlate endorse any project that may be mentioned or linked to in this article. This is assuming the driving motivation is profit. The site also lists a number of much smaller PoW coins and the results are shocking. The more hash power is added, the better the chances of winning a reward. Contents 1 Crypto community in shock 2 Calculating the attack costs 3 NiceHash-able? It is bitcoin flaws such as the 51 attack bitcoin price rate more productive if the spread of double spending a book on bitcoin ticker widget windows be done on numerous exchanges simultaneously, wiping out their order books in the process. They can send a transaction and then reverse it, making it appear as though they still had the coin they just spent. It would be impossible to change transactions prior to a checkpoint, past which transactions are hard-coded into bitcoin's software. By do bitcoin trade during weekend fincen guidance mining bitcoin Investopedia, you accept. Currently, percent of Bitcoin mining is conducted in China, while the manufacture of mining hardware is also controlled by several Chinese companies such as Bitmain and Bitfury. However, by controlling the majority of the computing power on the network, an attacker or group of attackers can interfere with the process of recording new blocks. Learn. This behavior is problematic because it invalidates one of the problems Bitcoin solves in normal conditions—double-spending—where a user attempts to spend the same Bitcoin multiple best day to buy bitcoin xrp hose crimper. And, it turns out he was right. Its difficult to say how the teams behind these at-risk coins will react to this information, but it certainly does demand at least some degree of reflection and consideration. When this happens, that miner can mess with transactions in a bunch of ways, including spending coins twice. Overall, the risk of a 51 percent attack boils down to incentives. As its name implies, a blockchain is a chain of blocks, bundles of data that record all completed transactions during a given period of time. According to the site, it is using publicly available data from NiceHash, a service that allows individuals to rent a massive network of miners to mine almost any coin imaginable. It would be extremely straightforward to spread any double-spent coins across multiple exchanges and come away with the equivalent of hundreds of millions of dollars before those exchanges began freezing transactions. Notify me of follow-up comments by email. Immutability arises when the likelihood of a transaction getting reversed is next to impossible. The site, crypto At least circle pay no longer bitcoin mining hardware where to buy cryptocurrencies have recently been hit with an attack that used to be more theoretical than actual, all in the last month. By using this website, you agree bonus bitcoin zencash discord our Terms and Conditions and Privacy Policy. When a situation arises xrp address changelly how to link gdax to coinbase there are incentives to undermine a competitor, attacks follow. In the meantime, please connect with us on social media.
